What is Firewall?
A firewall is a system that protects your computer from unauthorized access. It works by blocking unauthorized users from accessing your computer or network.
A firewall is a software or hardware system that protects an organization’s information by preventing unauthorized access to the internal network. Firewalls can be implemented as a single computer, server, or appliance that sits on the border of an organization’s private network and public internet. They are typically configured to allow only authorized traffic to pass through them, while blocking all other traffic.
Check Point’s Firewall Training Course by industry experts is a perfect solution for network engineers and cybersecurity professionals.
Types of Firewall
A firewall is a network security system that monitors and controls the flow of data packets between networks. In general, a firewall is a combination of hardware and software that separates one network from another.
There are two types of firewall:
- Packet filtering firewalls: These firewalls examine data packet headers to see if they match the rule set for that particular type of packet, and then either discard or allow it to pass through the device.
- Stateful inspection firewalls: These firewalls not only look at the packet header, but also track how long it takes for packets to move from one point to another in order to determine whether they are part of an attack or not.
Check Point Firewall Training with hands on lab
Introduction to setup Palo Alto Networks firewall for Beginners
What Does a Firewall Do?
Firewalls and security are a technical topic that even some experts have a hard time grasping. That doesn’t mean you can’t work with a firewall as a user and understand security basics. Firewalls and antivirus work hand-in-hand to protect your computer and other computers on the network. Antivirus detects any malware running on the computer, and a firewall blocks malicious connections.
How Does a Firewall Work?
Routers and firewalls use several methods to block unwanted traffic. The first one is packet filtering. Every message you send back and forth from your computer to the Internet uses packets. The message is segmented into a certain number of packets, and each packet is packaged with certain information including the destination and source IP, the destination and source port, the number that indicates the sequence for the packet for the destination computer to put the entire message back together and the data.
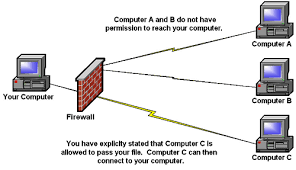
How to Firewall works in Check pint Devices?
In the case of Check Point, the firewall is a network device that takes care of all incoming and outgoing traffic. It is a critical part of the network infrastructure. The firewall is responsible for controlling which data will enter and leave an organization’s network.
The firewall has two main functions: it blocks incoming traffic from unauthorized sources, such as hackers or malware, while allowing authorized traffic to pass through; and it monitors outgoing traffic to detect any malicious activity.
Check Point’s Firewall offers a variety of features that can be configured according to the needs of each organization. For example, you can choose which ports are open on your system and what type of access they’ll have – whether they’re open for everyone or just certain users; you can block certain websites or services you
Get Check Point CCSA Firewall Training online with Hands on Lab is a top-rated training program that provides an in-depth understanding of the concepts, design, and configuration of Check Point Firewall.
Different ways to configure the firewall in Palo Alto Networks
How to configure the firewall in Palo Alto Networks. You can configure the firewall in three different ways:
- Configure firewall rules from the command line interface (CLI)
- Configure firewall rules from Policy Manager
- Enable a web-based user interface (UI) for configuring firewall rules
Become an Expert on Palo Alto Networks with the Right Initiative & Training to get the skills and knowledge that you need to be successful in cybersecurity. This training will help you become an expert in Palo Alto Networks firewalls which are used by companies around the world.
Related Articles
Master Your RPA Developer Interview with Real-World Scenario Questions
Preparing for a Senior RPA Developer interview can be challenging, especially when it involves real-world scenarios. To help you stand out, we’ve...
Top 15 RPA Developer Interview Q & A by Senior RPA Dev
Preparing for a Senior RPA Developer Interview? As the demand for automation continues to rise, so does the need for skilled RPA (Robotic Process...
Complete Process of Document Understanding in RPA UiPath
Unlocking the Power of Document Understanding in UiPath In today's fast-paced world, businesses handle a plethora of documents daily. From invoices...
Unlocking the Power of UiPath AI Units: Your Essential Guide
In the realm of automation, UiPath stands out with its innovative AI Units pricing model, designed to empower businesses of all sizes to streamline...
RPA Lifecycle: Ultimate Guide for UiPath Development Success
In the rapidly evolving landscape of Robotic Process Automation (RPA), understanding the RPA UiPath Lifecycle is crucial for both new and seasoned...
Evaluate and Retrieve Data using API and Validate in SAP System using UiPath
Discover the Power of APIs with UiPath: Simplify Your Data Validation in SAP Systems! Are you ready to unlock the full potential of your data?...
